Stop fake accounts. Protect real ones.
Castle's lightweight API lets you block large-scale bot attacks, fake signups, and account takeovers — all without the hassle of CAPTCHAs.
Invisibly shield your accounts from threats
Go beyond CAPTCHAs with a lightweight API that blocks large-scale human and bot-driven attacks using user identity, reputation, and behavior analysis.
-
Lightweight integration
Integrate Castle as easily as adding a CAPTCHA, without routing all web traffic through a CDN.
-
Complete protection
Prevent large-scale attacks, detecting both human and bot-driven account takeovers and fake signups.
-
No CAPTCHAs needed
Leveraging user identity, reputation, and behavior, Castle blocks attackers without CAPTCHAs that can tip them off.
- Robotic input
- 3 accounts per device
- Residential proxy
- No internet history
- Newly registered domain
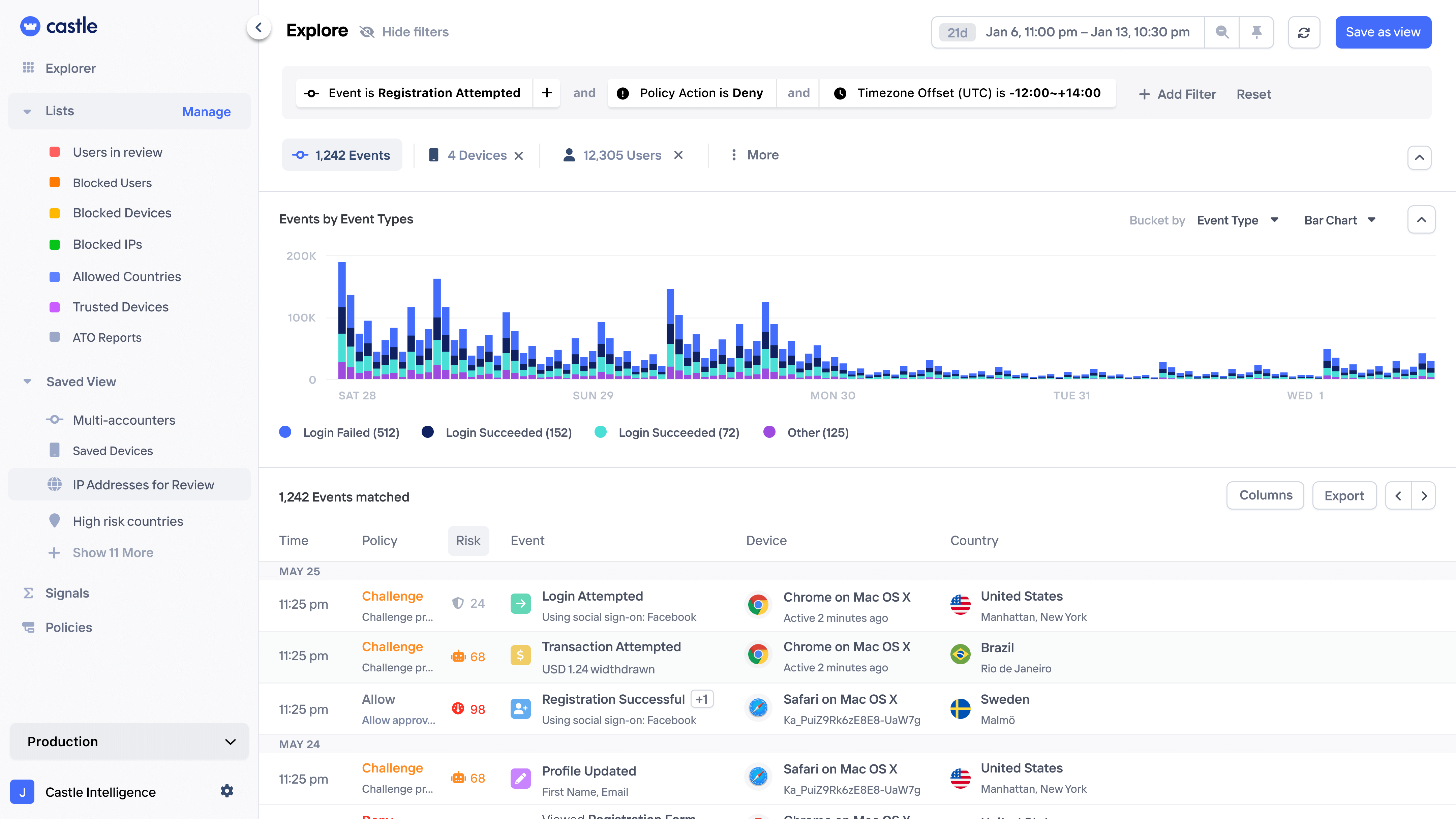
Stop any abuse with a single, unified API
Get comprehensive threat insights in real-time, eliminating the need for multiple, disconnected tools.
|
|
Built for scale
Our APIs process billions of monthly requests with resilience against severe bot attacks.
100ms response time
Fingerprinting, risk scores, and rules computed instantly in real-time.
Pay-as-you-go pricing
Transparent and predictable plans based on requests or MAU.
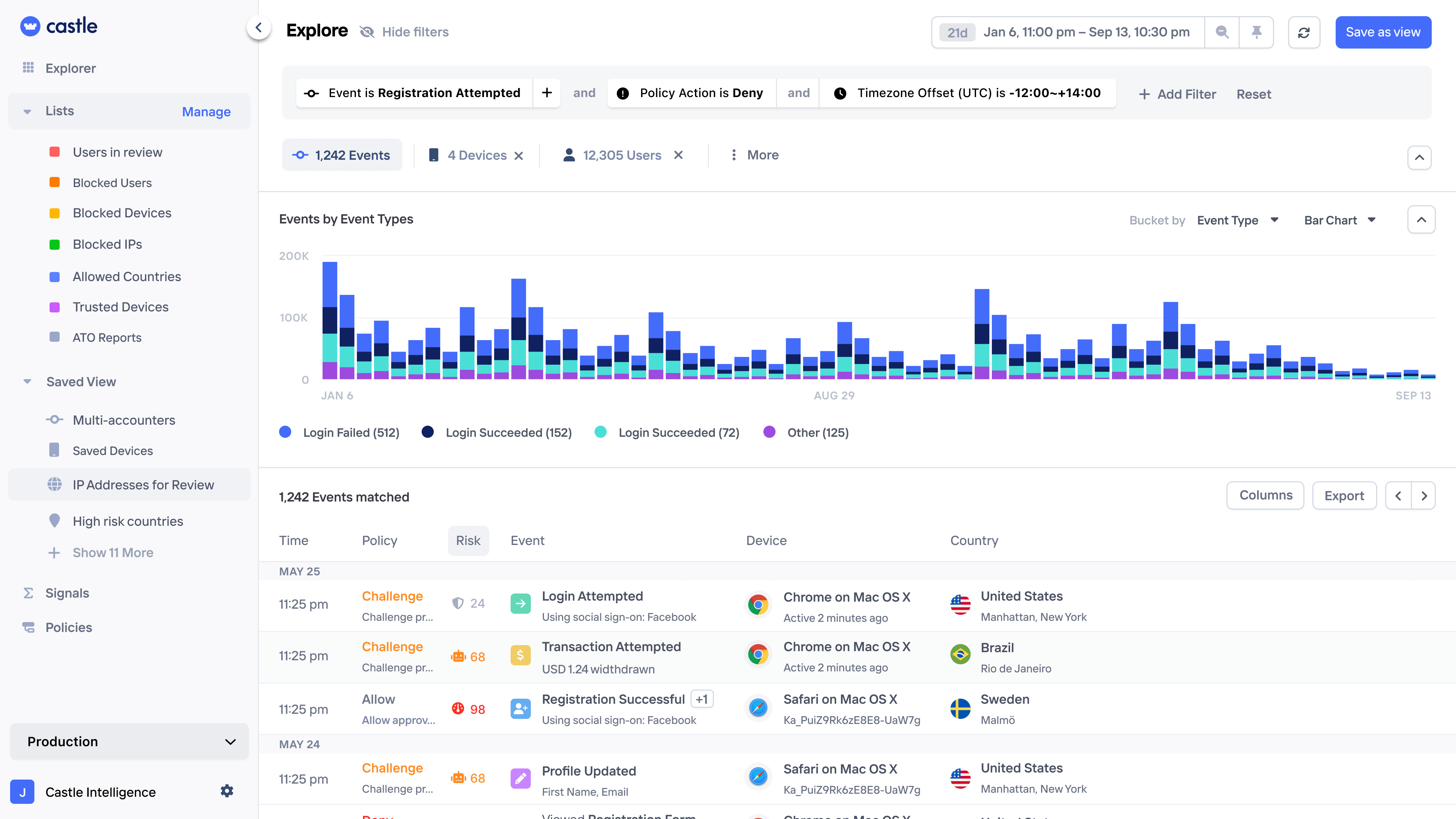
Uncover hidden abuse patterns proactively
Monitor, analyze, and alert on up to 18 months of historical data enriched with user and device intelligence to stop evolving abuse trends.
Network analysis
Spot network of bad user activity via shared devices, emails, IPs, payment methods, or addresses.
Pattern exploration
Uncover bad user activity by querying and visualizing large amounts data and turn into rules with a few clicks.
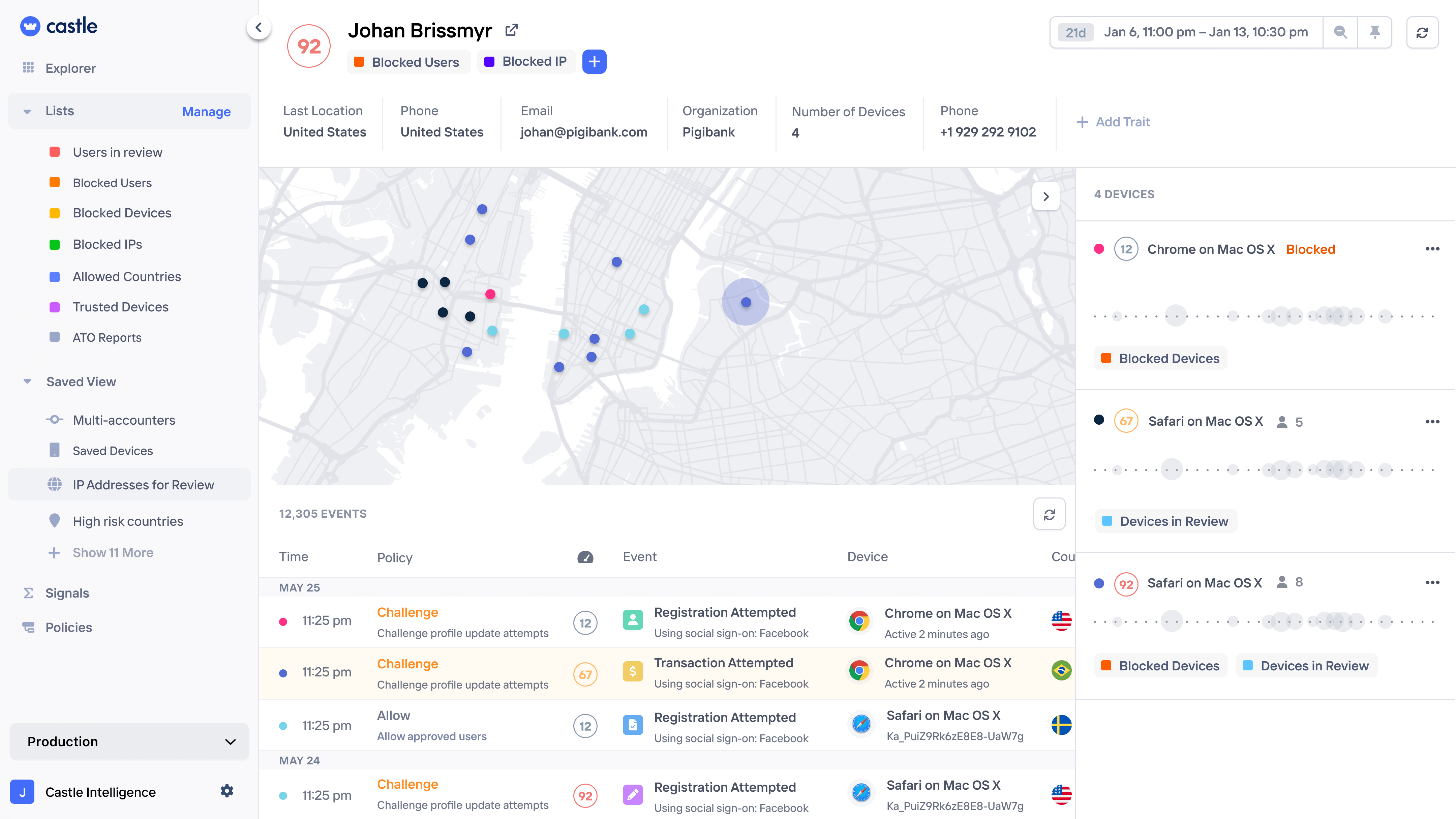
Session monitoring
Get a complete history of each user and company, down to individual page views and any custom actions.
Rule backtesting
Test complex risk logic on historical data first, ensuring zero disruption to legitimate users.
Pattern exploration
Uncover patterns in on login attacks, signup spam campaigns, and repetitive in-app transactions.
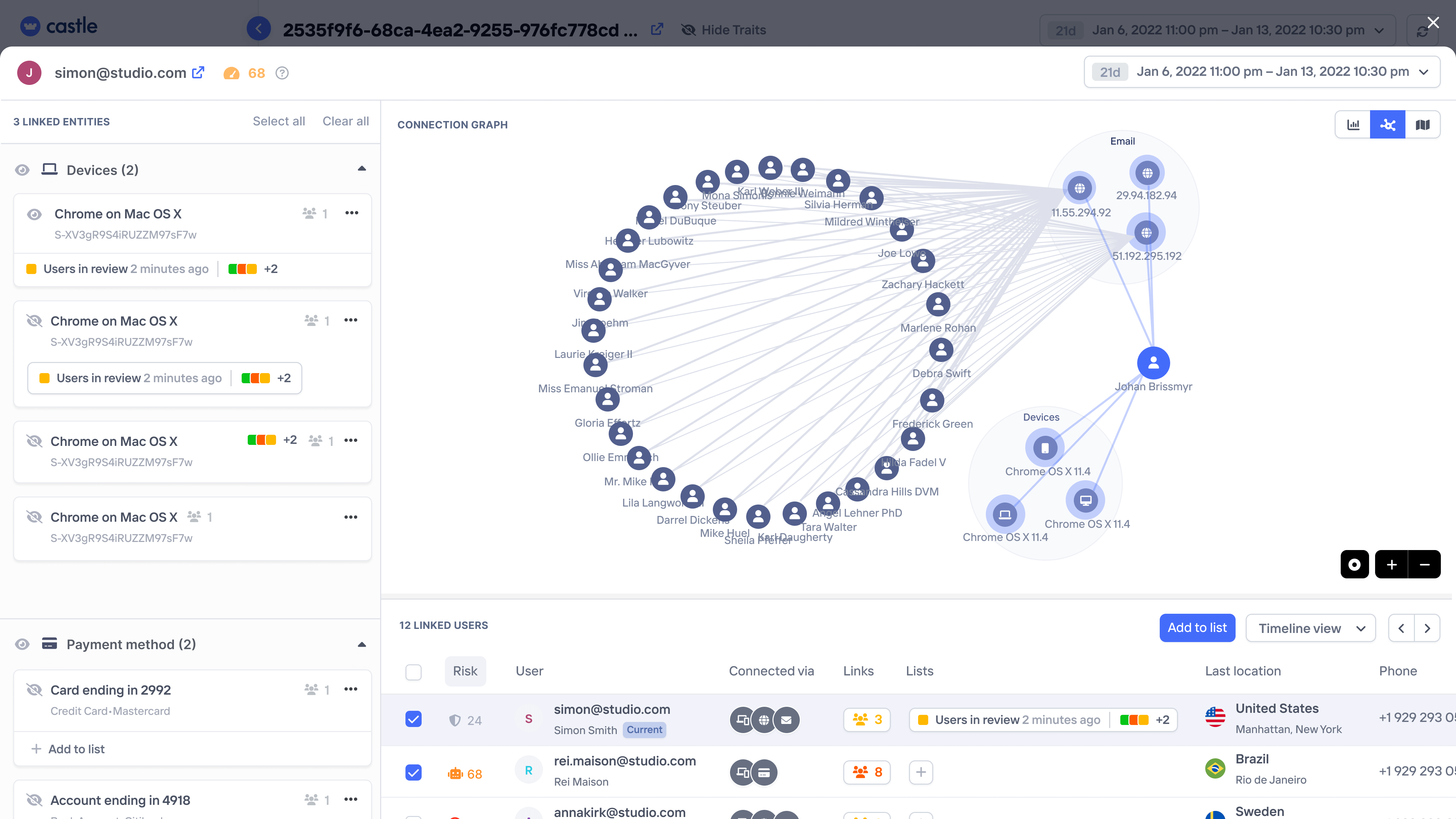
Network analysis
Spot interconnected users via shared devices, emails, IPs, payment methods, or addresses.
Session monitoring
Get a complete history of each user and company, down to individual page views and any custom actions.
Rule simulation
Test complex risk logic on historical data first, ensuring zero disruption to legitimate users.
Turn analysis into action with a click
End inefficient workflows with seamless analysis-to-rules conversion. Block any abuse with custom rules built on rich data and real-time aggregations.
Weed out bad actors before or after signup
Segment out new accounts based on similarity to other accounts, bot behavior, and blocklists.
More about Fake Accounts

- Suspicious IP
- Users per Device (12)
- Repetitive Email Pattern
- Abuse-repored IP

- Suspicious IP

- Blocked Country
Identify both bots and human attacks
Use a combination of scores and heuristics to highlight suspicious or hijacked accounts.
More about Account Takeovers

- Credential Stuffing
- New Device
- Datacenter IP
- Abuse-repored IP

- New Device
- New Country
- Impossible Travel

- Proxy IP
- Users per Device (2)
Only allow signing up once
Aggregate the number of accounts created per device, IP, or credit card and block when it exceeds a threshold.
More about Multi-Accounting

- Users per Device (13)
- Users per Credit Card (7)
- Users per IP (32)

- Users per Device (12)
- Users per Credit Card (6)
- Users per IP (31)

- Users per Email (3)
Block repetitive spam content
Customize logic based on the the number of content posts or messages per device and minute, and tune it with regex filters.
More about Content Abuse

- Bot Behavior
- Content per IP (122)
- Datacenter IP

- Content per User 1h (33)
- Proxy IP

- Blocked Regex
Eliminate SMS verification abuse
Use a mix of bot detection and velocity signals to lock down spammy SMS fees with high precision
More about SMS Pumping

- Bot Behavior
- Verifications per IP (48)
- Users per Device (12)

- Bot Behavior
- Verifications per IP (48)

- Blocked Phone Numbers
Define account sharing your way
Uncovering account sharing requires granular controls to define the exact behavior that breaches your terms of services.
More about Account Sharing

- Excessive Content Sharing
- Impossible Travel

- Frequent Device Toggling
- Bot Behavior
- Proxy IP

- Frequent IP Toggling
- Impossible Travel
Stop card testing before the transaction
Implement velocity checks to prevent a transaction attempt from reaching your payment processor in the first place.
More about Transaction Abuse

- Transactions per 1h (13)
- Transactions per Card (21)
- Users per Device (3)

- Transactions per 10m (5)

- Blocked Credit Card
Headless API protection
Castle supports protection of endpoints where client-side code can't be injected, such as desktop apps or REST APIs
More about API Abuse

- Request per IP (138)
- Abuse-reported IP
- Time Since Registration (39s)

- Request per User (18)

- Blocked IP
Scale abuse response with custom flows
Model custom security flows, blocklists, and trusted device management. Manage states across signup, login, transactions, and more – manually for investigations or automate actions with our rules engine. Empower users to report abuse and streamline your team's review processes.

State management
Maintain custom security lists (blocklists, allowlists, trusted devices, reviews, etc.) and update states in real-time based on rules and manual actions.
Inline blocking
Initiate real-time blocks or step-up verifications anywhere in your app without disrupting the user experience.
Alerts & notifications
Ensure your team stay informed with triggered Slack notifications, or automate end-user notifications or internal processes using granular webhooks.










