Blog #1 in a 4 Blog Series on Attack Tactics that Increase Success Rates… And What You Can Do to Thwart Them

Leaf-tailed geckos know their chance of survival goes way up, if they can’t be found. They have perfected the art of blending in, making themselves hard to spot amongst the flora and fauna of their home in Madagascar.
Attackers are much the same. They know that if they can blend into normal traffic patterns, they have a better chance of not just surviving, but thriving. It’s why they target your users – if they can takeover a user’s account, they can camouflage all their activities under that user’s identity. They can login and operate undetected, which means they can do almost anything:
- Steal sensitive data
- Complete financial transactions
- Hold data or accounts ransom
- Disrupt normal operations
- Launch other attacks (download or remotely execute code to accomplish other attack objectives)
Gartner estimates online fraud costs organizations over $5 billion. The first step to identifying and stopping these attacks is understanding how they are perpetrated. We’ve uncovered four tactics attackers are increasingly using to try to fly under the radar and increase the success rates of their account takeover attacks.
This is the first in a four-part blog series that will look at each of these tactics and provide tips to mitigate the risks they introduce.
Tactic #1: Use More IPs to Look Like More Users
Attackers are spreading out their activity, using large number of IPs to disguise who they are and what they are doing. In essence, they appear to come from everywhere, so they are noticed by no one.
Watch the below quick 1-minute video to see an example of this type of attack.
Typically, one IP address corresponds with one user. Sometimes, an IP can be traced down to the street-level of a particular user. Thanks to IPv6 and the proliferation of cloud services, IPs are easier and cheaper than ever to get, enabling an attacker to use many different IPs, in many different locations, to look like many different users.
These IPs come from a couple of sources:
- Datacenter proxies: typically provided by hosting companies. They give attackers some anonymity, as well as the use of fast, stable, reliable connections.
- Residential proxies: assigned by telecommunications to residents for personal home use. They aren’t as fast or reliable as datacenter proxies, but they can be used to further distribute attack traffic and will make it harder for the target site to block.
- Botnets: huge networks of hacked devices, under the control of an attacker, consisting of almost anything connected to the Internet, from computers and security cameras to refrigerators and coffee makers. They provide attackers pure mass compute power and a highly distributed network.
Example – the difference 59,998 IPs can make
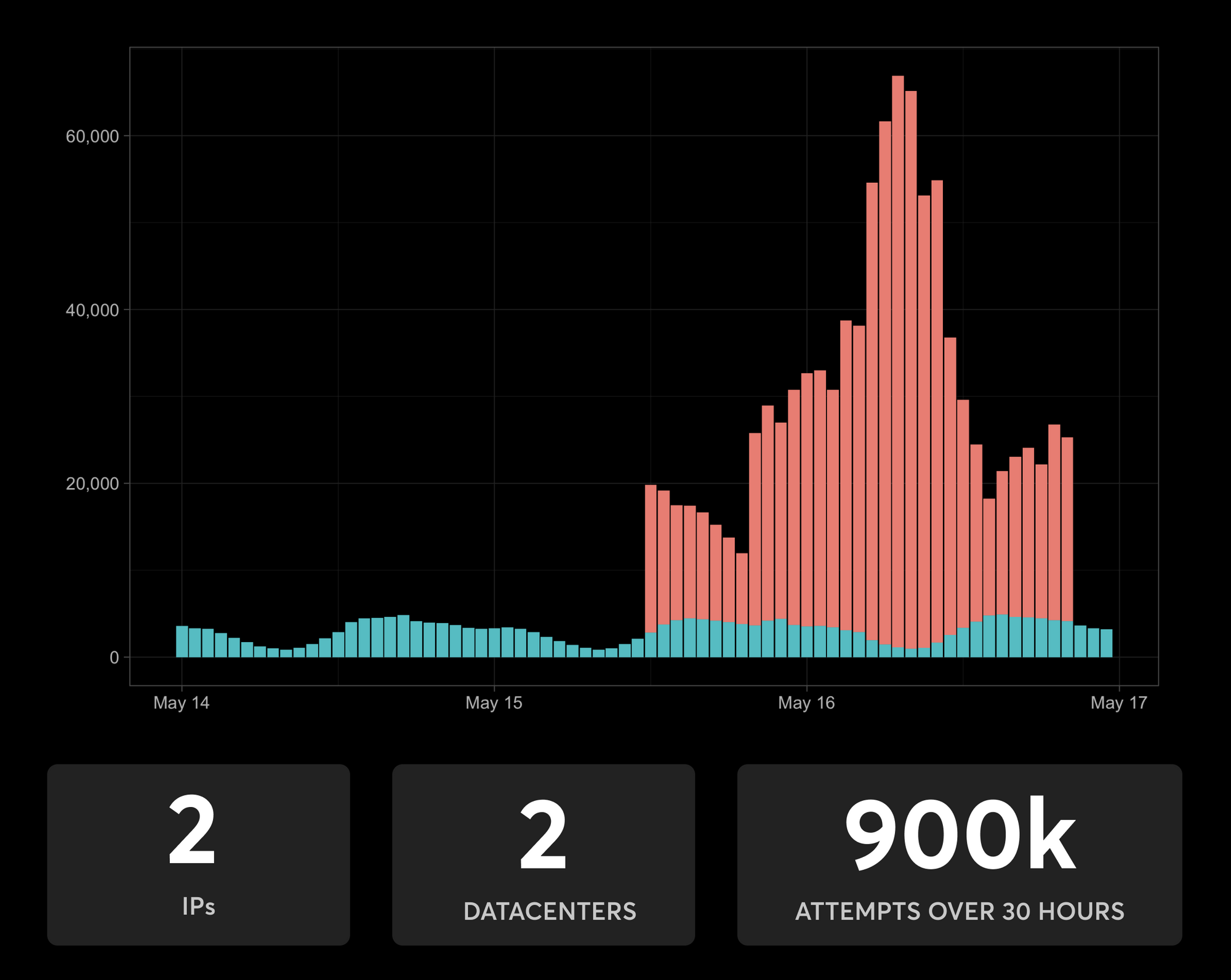
For example, a site that usually has 2000 to 5000 events an hour (blue trend lines in the graph on the right), will notice if all of a sudden there are 900K login attempts (red trend lines in the graph on the right), coming from two IPs and two datacenters. This obvious spike is easy to identify and shut down, using:
- IP rate limiting: limits the number of connections that can come from an IP; once the limit is reached, all subsequent connections will be blocked
- Blacklisting: blocks IP address known to be malicious
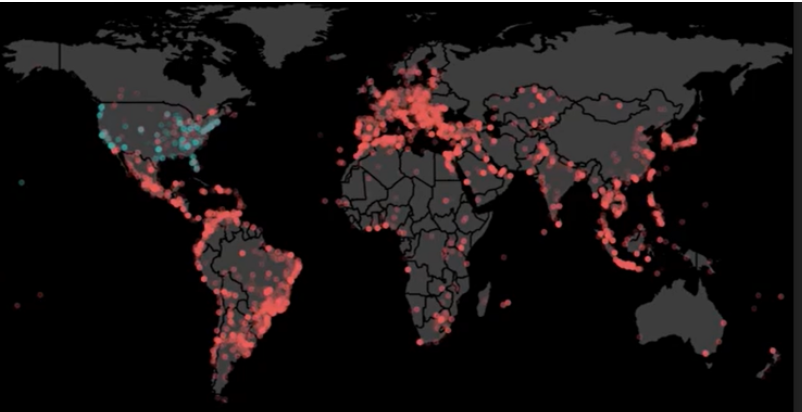
But, when an attacker spreads out their traffic, such as the attack depicted on the right, it is much more difficult to spot. This attack used 60K IPs in 210 countries to complete 700K login attempts over 10 hours. Even though the site saw upticks in failed logins over the course of the attack, three failed login attempts per hour, per IP didn’t raise much suspicion in isolation. Normal rate limiting and blacklisting mechanisms didn’t have any affect because the attack was spread over so many unique IPs – many of which were being used for the first and last time. It was only when the site looked in aggregate at all the traffic they were able to spot what was happening. Ultimately, the attacker got more than 700 validated credentials, which they can use to perpetrate an attack.
The Answer?
Because attackers are distributing their activity over thousands of IPs located around the world, they are much harder to spot and harder to stop with traditional rate limiting and blacklisting techniques. It takes finesse and sophisticated technologies (because it’s not practical to rely on manual intervention) to prevent. Look for solutions that can:
- Decipher suspicious traffic from normal traffic patterns
- Understand user and device behavior
To learn more about this account takeover tactic and several others that we uncovered, download our ebook “Evolution of Attacks on Online Users.”
For more information about Castle's customer identity and access management capabilities or to start a free trial, please go to https://castle.io/.







