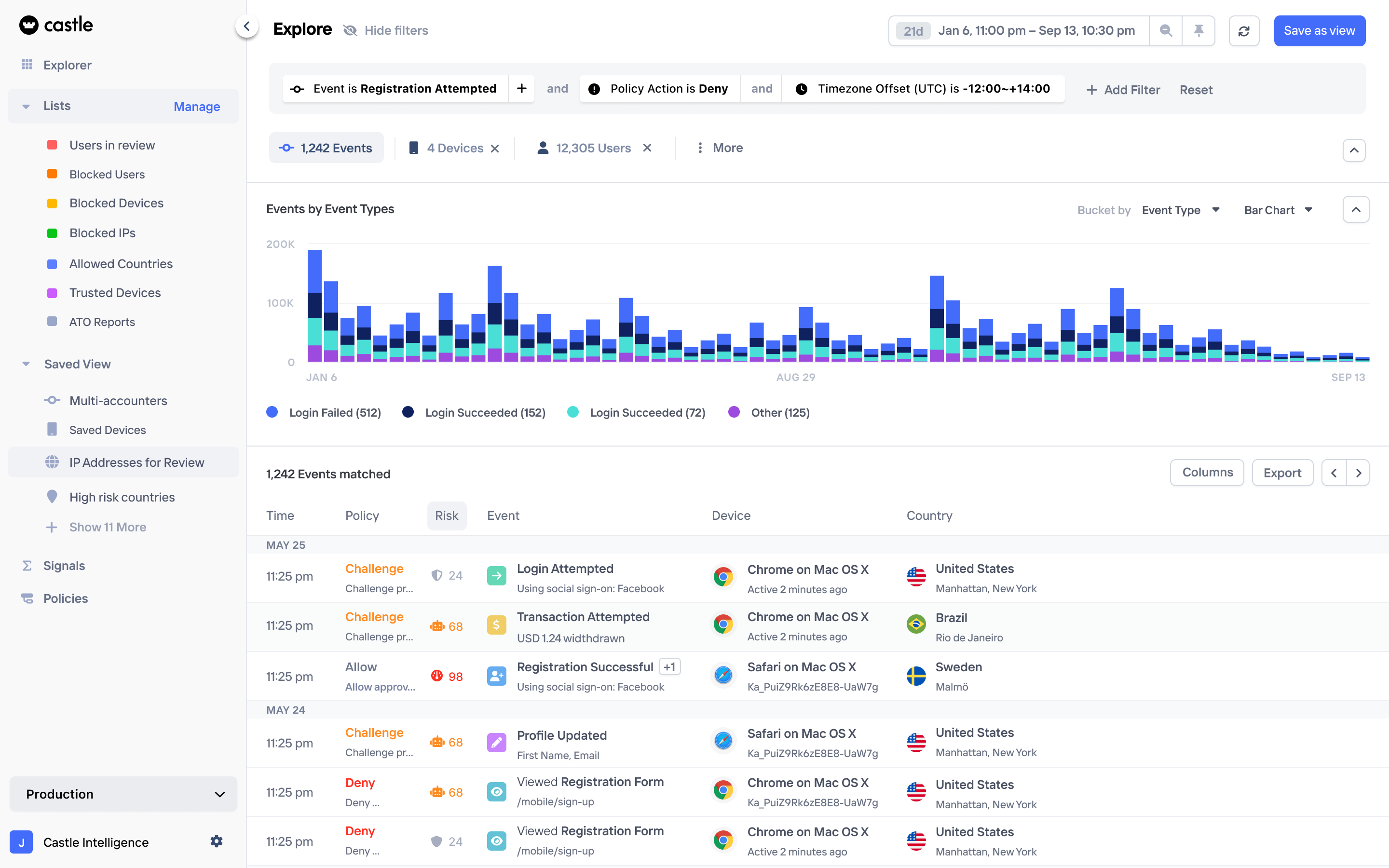
Stop bots and account abuse in minutes
Connect Castle to Cloudflare with no code, or use your own edge stack. Use the SDK to monitor users and stop fraud in-app. Enterprise security without the friction.
Dual-layer fraud defense
Castle is natively built to run at the edge and in-app as one system. Signals flow between both, so what you block early sharpens what you catch later.
-
Block abuse at the edge
Deploy Castle at the edge to analyze every request and credential stuffing and scripted abuse before they reach your backend.
-
Catch fraud in the app
Add our SDK to track sessions, devices, and behavior, enriched with your own business context. Spot fake signups, account takeovers, and multi-accounting in real time.
-
Go live in minutes
Start in monitoring mode, switch to blocking when ready. No DNS swap. No contracts. Just connect, observe, and protect.
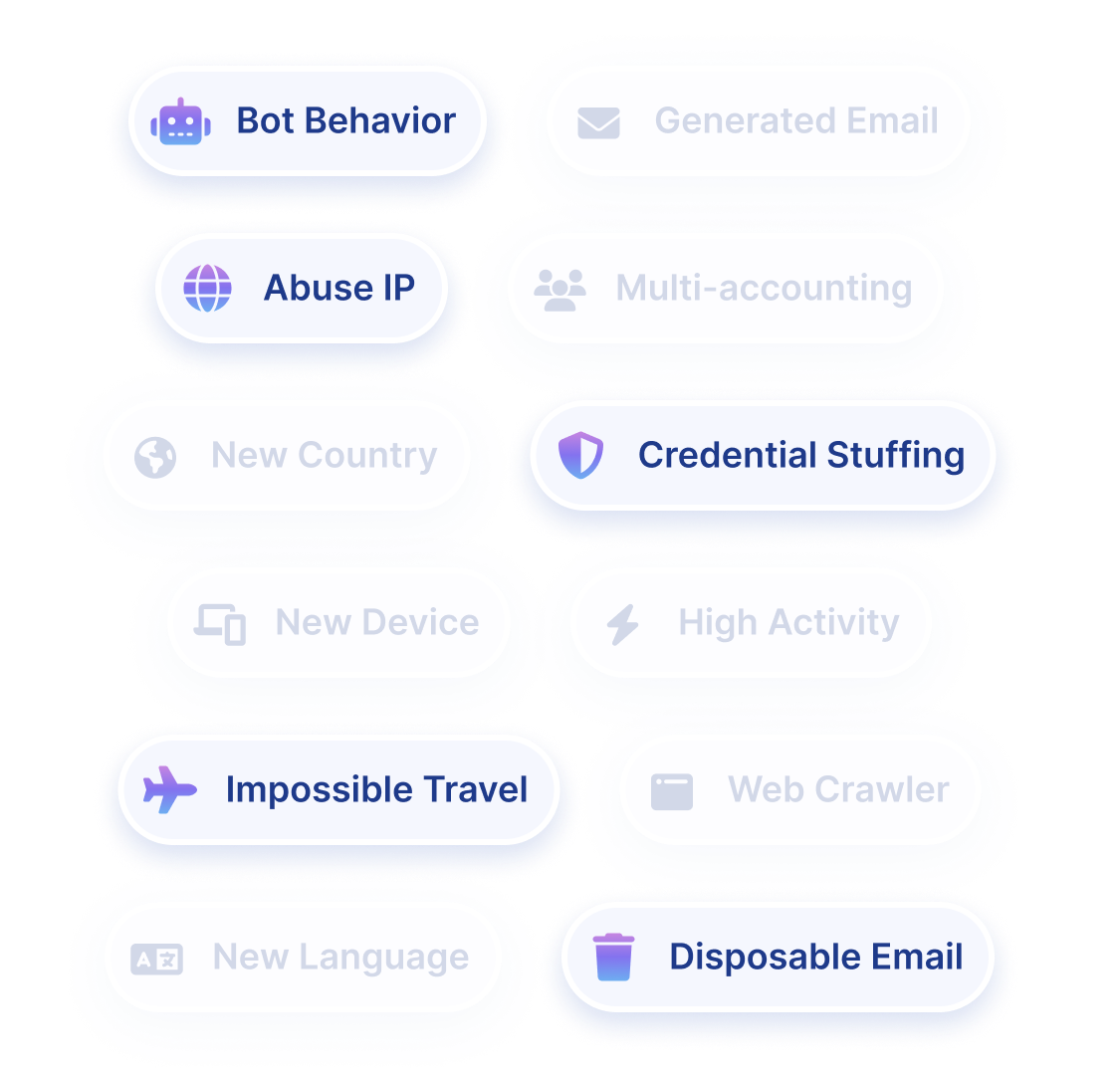
- Robotic input
- 3 accounts per device
- Residential proxy
- Spiky behavior
- Newly registered domain
Everything you need to stop fraud & abuse
A complete stack of data, tools, and APIs, eliminating the need for multiple, disconnected tools.
-
Behavioral analysis
Use out-of-the-box signals or create your own custom aggregations and rate limiters.
-
Device fingerprinting
99.5% accurate fingerprinting. Uncover headless browsers, tampering, carrier data, etc.
-
Bot detection
Detect bots, scripts, and coordinated attacks. Identify automated behavior and tampering.
-
AI scoring
Spot account takeover attempts and abusive behavior using self-learning AI.

-
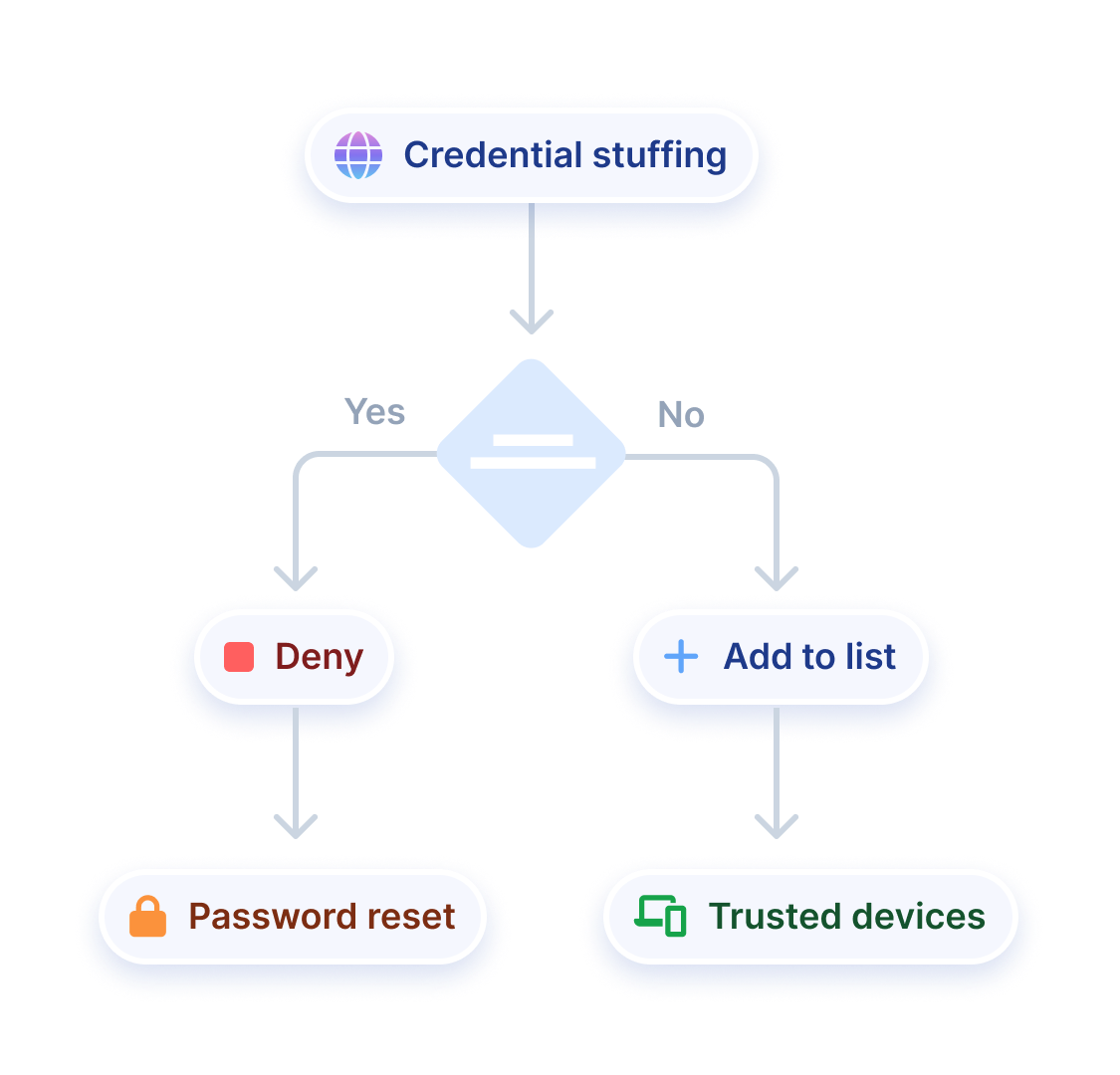
Rules engine
Real-time allow, challenge, or deny actions. Manage rules seamlessly, without code changes.
-
Email intelligence
Assess email reputation and risk. Detect disposable domains and enumeration patterns.
-
Case & state management
Manage dynamic trust, block, and review lists of users, devices, or any custom attribute.
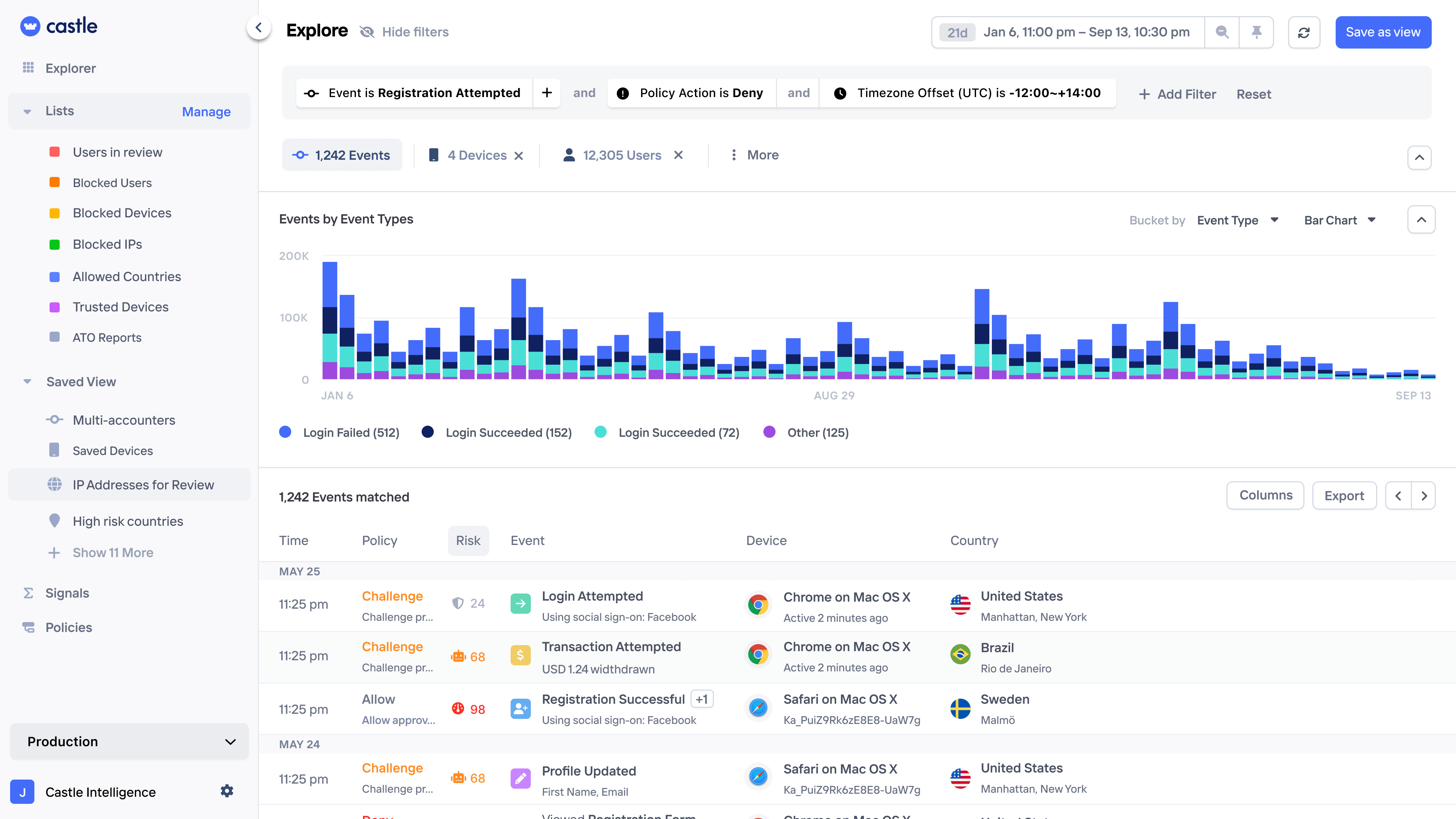
Proactive threat hunting with user behavior analytics
Monitor, analyze, and alert on up to 18 months of historical data enriched with user and device intelligence to stop evolving abuse trends.
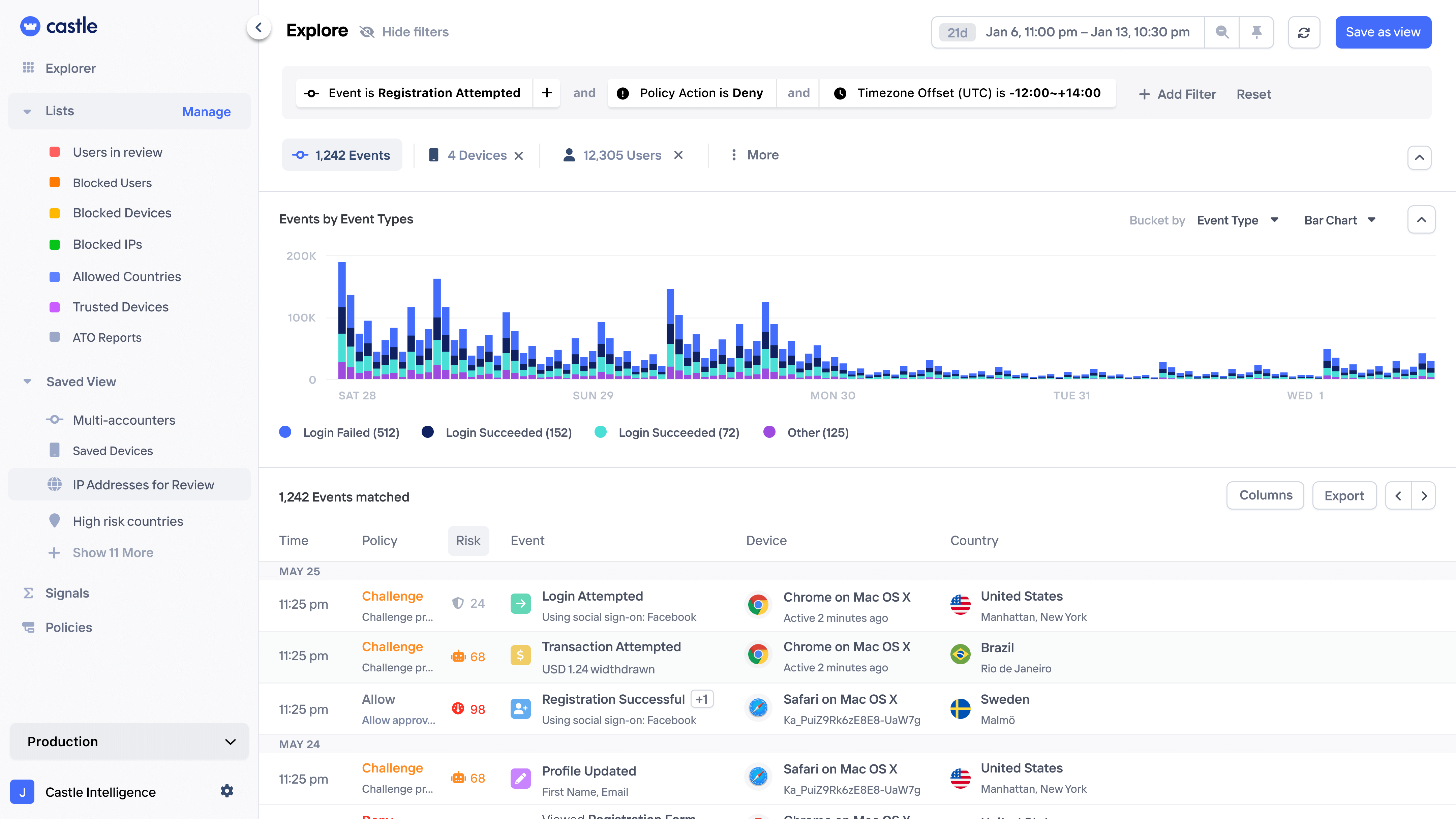
Network analysis
Spot network of bad user activity via shared devices, emails, IPs, payment methods, or addresses.
Pattern exploration
Uncover bad user activity by querying and visualizing large amounts data and turn into rules with a few clicks.
Session monitoring
Get a complete history of each user and company, down to individual page views and any custom actions.
Rule backtesting
Test complex risk logic on historical data first, ensuring zero disruption to legitimate users.
Pattern exploration
Uncover patterns in login attacks, signup spam campaigns, and repetitive in-app transactions.
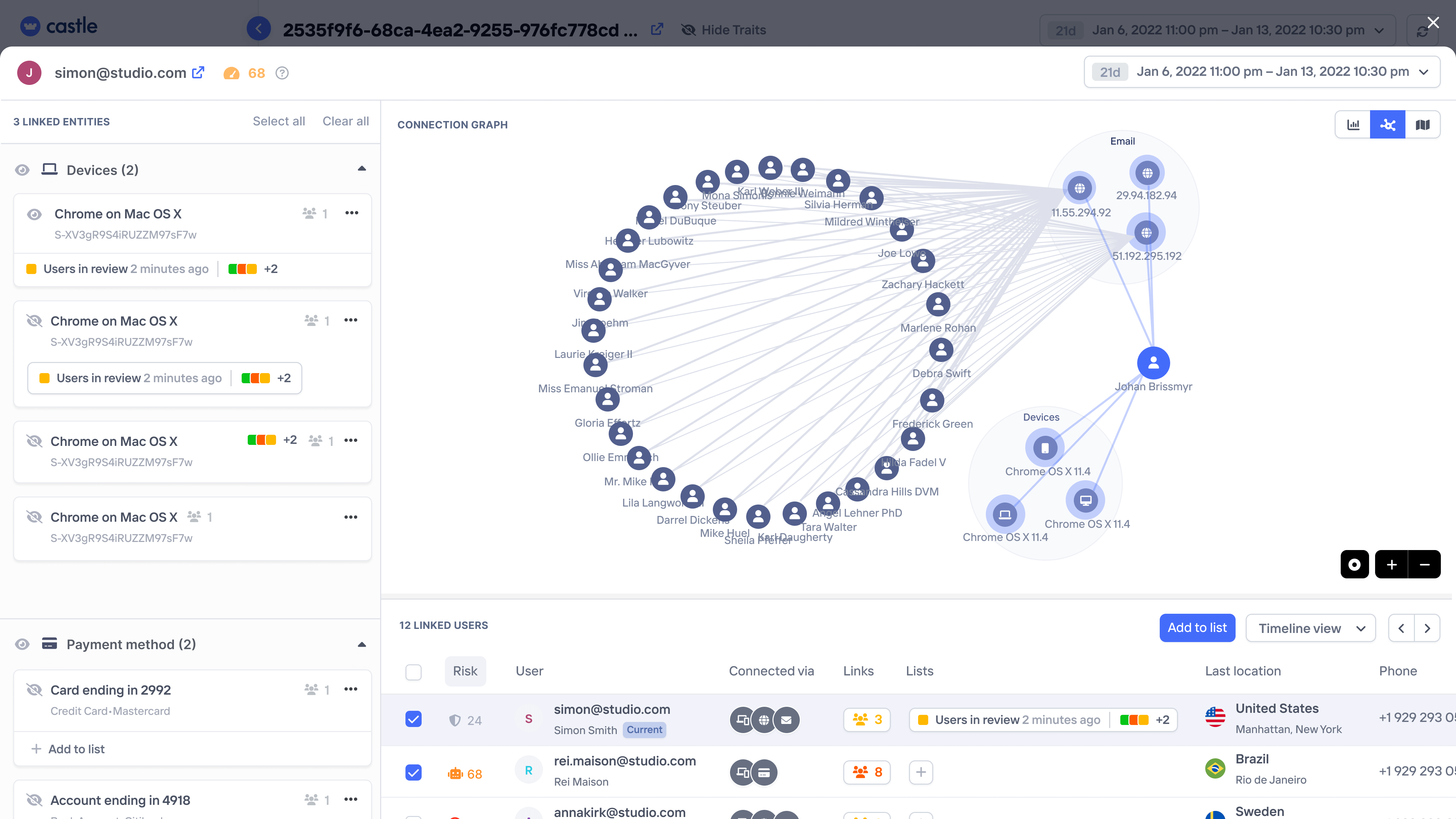
Network analysis
Spot interconnected users via shared devices, emails, IPs, payment methods, or addresses.
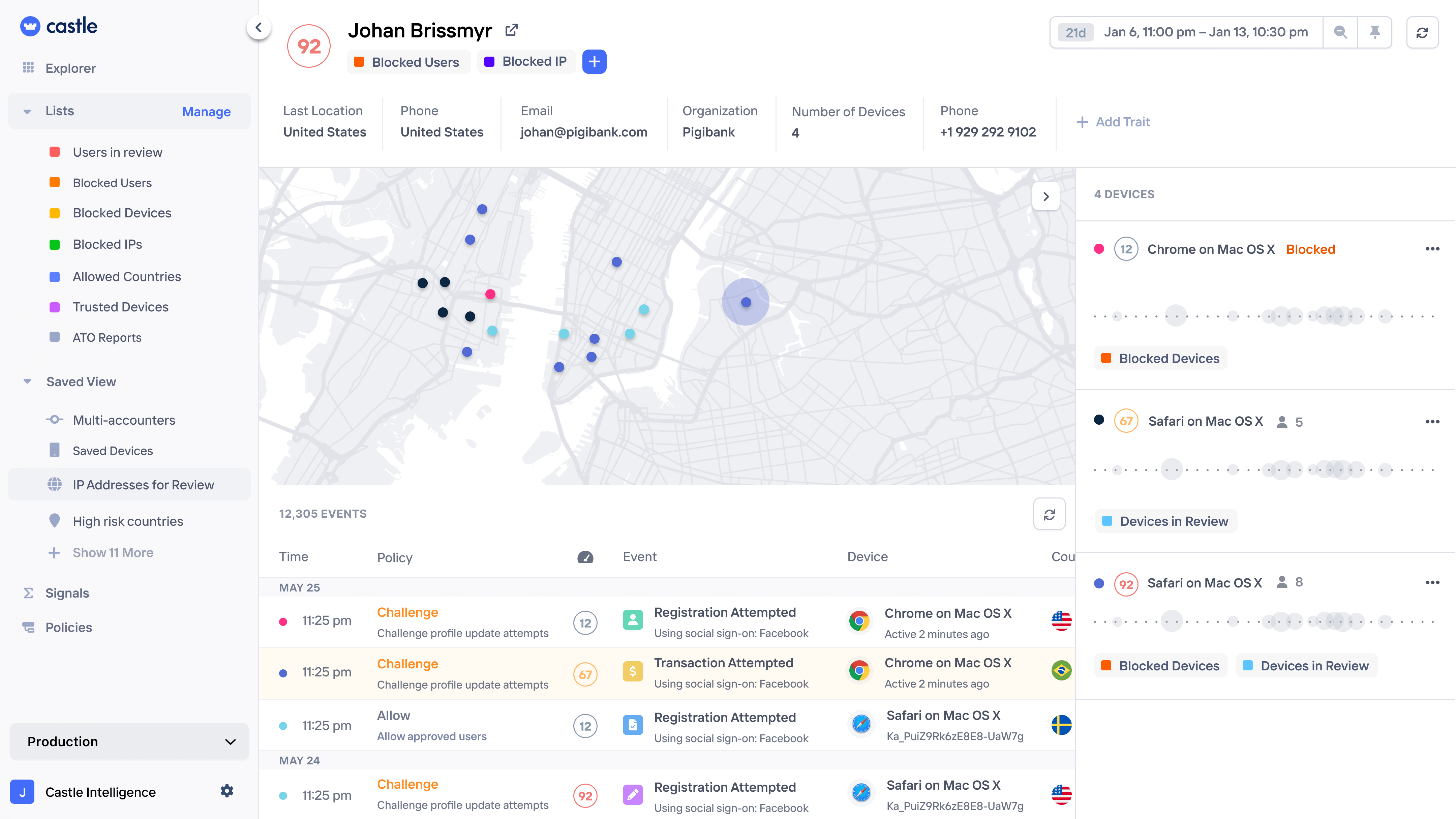
Session monitoring
Get a complete history of each user and company, down to individual page views and any custom actions.
Rule simulation
Test complex risk logic on historical data first, ensuring zero disruption to legitimate users.
Fraudulent behavior, as defined by you
Combine Castle's threat data with velocity checks and rate limiters to categorize users according to what's considered fraud and abuse on your specific platform.
Weed out bad actors before or after signup
Segment out new accounts based on similarity to other accounts, bot behavior, and blocklists.
More about Fake Accounts

- Suspicious IP
- Users per Device (12)
- Repetitive Email Pattern
- Abuse-repored IP

- Suspicious IP

- Blocked Country
Identify both bots and human attacks
Use a combination of scores and heuristics to highlight suspicious or hijacked accounts.
More about Account Takeovers

- Credential Stuffing
- New Device
- Datacenter IP
- Abuse-repored IP

- New Device
- New Country
- Impossible Travel

- Proxy IP
- Users per Device (2)
Only allow signing up once
Aggregate the number of accounts created per device, IP, or credit card and block when it exceeds a threshold.
More about Multi-Accounting

- Users per Device (13)
- Users per Credit Card (7)
- Users per IP (32)

- Users per Device (12)
- Users per Credit Card (6)
- Users per IP (31)

- Users per Email (3)
Block repetitive spam content
Customize logic based on the the number of content posts or messages per device and minute, and tune it with regex filters.
More about Content Abuse

- Bot Behavior
- Content per IP (122)
- Datacenter IP

- Content per User 1h (33)
- Proxy IP

- Blocked Regex
Eliminate SMS verification abuse
Use a mix of bot detection and velocity signals to lock down spammy SMS fees with high precision
More about SMS Pumping

- Bot Behavior
- Verifications per IP (48)
- Users per Device (12)

- Bot Behavior
- Verifications per IP (48)

- Blocked Phone Numbers
Define account sharing your way
Uncovering account sharing requires granular controls to define the exact behavior that breaches your terms of services.
More about Account Sharing

- Excessive Content Sharing
- Impossible Travel

- Frequent Device Toggling
- Bot Behavior
- Proxy IP

- Frequent IP Toggling
- Impossible Travel
Stop card testing before the transaction
Implement velocity checks to prevent a transaction attempt from reaching your payment processor in the first place.
More about Transaction Abuse

- Transactions per 1h (13)
- Transactions per Card (21)
- Users per Device (3)

- Transactions per 10m (5)

- Blocked Credit Card
Headless API protection
Castle supports protection of endpoints where client-side code can't be injected, such as desktop apps or REST APIs
More about API Abuse

- Request per IP (138)
- Abuse-reported IP
- Time Since Registration (39s)

- Request per User (18)

- Blocked IP
Scale threat response with custom flows
Model custom security flows, blocklists, and trusted device management. Manage review states across signups, logins, and in-app activity.

State management
Maintain custom security lists (blocklists, allowlists, trusted devices, reviews, etc.) and update states in real-time based on rules and manual actions.
Inline blocking
Initiate real-time blocks or step-up verifications anywhere in your app without disrupting the user experience.
Alerts & notifications
Ensure your team stay informed with triggered Slack notifications, or automate end-user notifications or internal processes using granular webhooks.
A single API to detect, score, and act. Everywhere.
Retrieve comprehensive threat insights in real-time and use them to tailor the user experience.
|
|
Built for scale
Our APIs process billions of monthly requests with resilience against severe bot attacks.
100ms response time
Fingerprinting, risk scores, and rules computed instantly in real-time.
Pay-as-you-go pricing
Transparent and predictable plans based on requests or MAU.
Create your free account today
Starting at $0 for 1,000 requests per month, with transparent pricing that scales with your needs.