Protect from account takeovers in minutes
Efficiently weed out account takeovers with a five minute Segment or Javascript integration.
Start for free
Real-time blocking
Rules execute in milliseconds to block Account Takeovers inline without noticable delay.
Custom definitions
Define Account Takeovers your way using advanced filtering and real-time velocity queries.
Granular analytics
Leverage BI-grade analytics to expose Account Takeovers and fraud rings at scale.
Data enrichment
Enriched with device intelligence, risk scores, velocity metrics, and much more.
Define account takeovers using custom logic
Castle lets you use advanced filtering, real-time velocity queries, and custom lists to segment out account takeovers with high precision.


- Credential Stuffing
- New Device
- Datacenter IP
- Abuse-repored IP

- New Device
- New Country
- Impossible Travel

- Proxy IP
- Users per Device (2)
Action on account takeovers in real-time
Rules execute in milliseconds and can be used to adapt the user experience based on risk in real-time.

Real-time decisions
Assessments of data like user count per device or hourly failed logins executed in the blink of an eye.
Inline blocking
Initiate request blocks or step-up verifications anywhere in your app without disrupting the user experience.
Alerts & notifications
Ensure your team and users stay informed with triggered Slack notifications or webhooks.
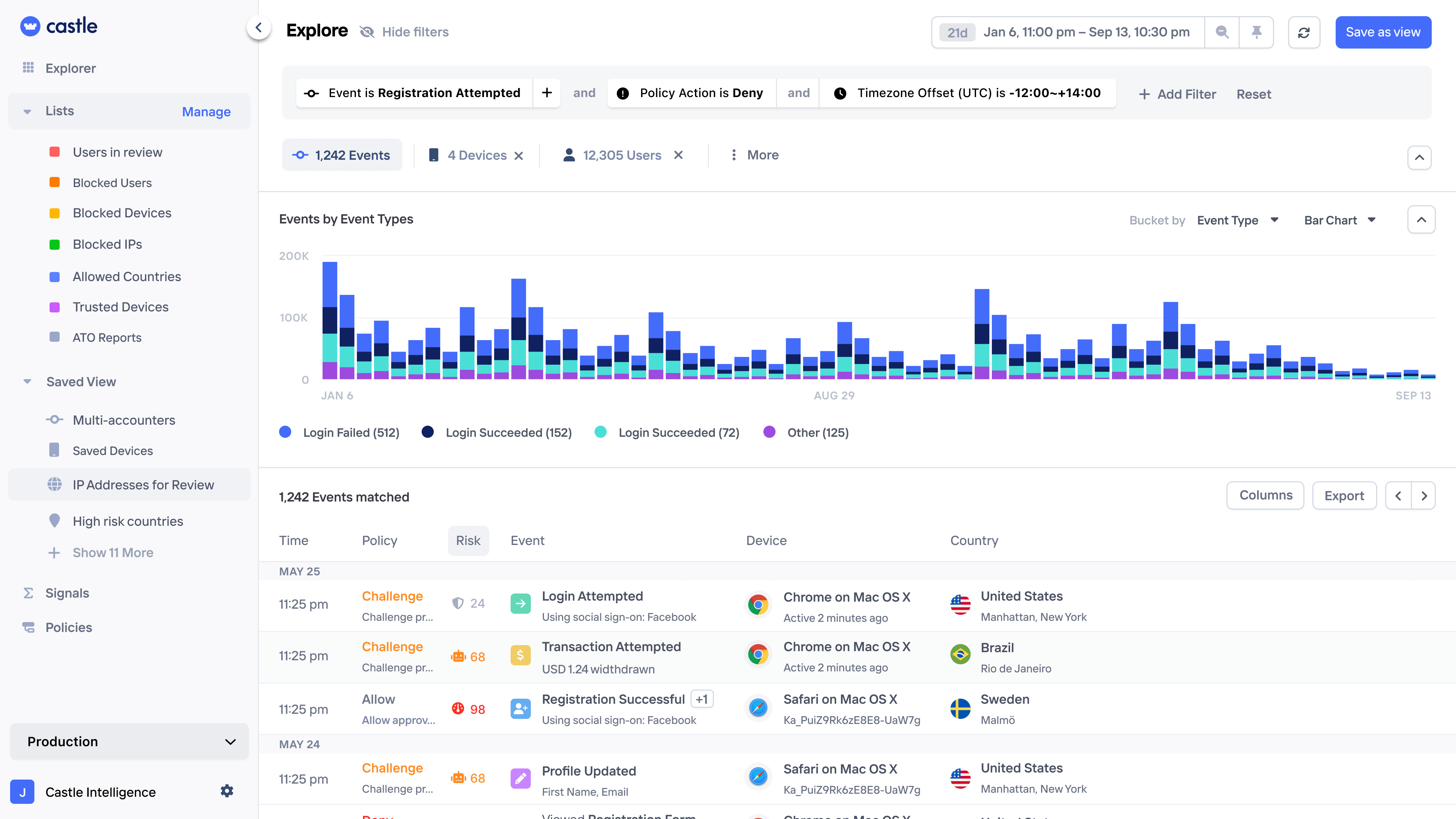
A holistic view
of account takeovers
Harness the power of BI-grade analytics to expose account takeovers attacks and unravel fraud rings with precision.
Pattern exploration
Query and visualize account takeovers at scale and turn the logic into rules with a few clicks.
Link analysis
Spot network of account takeovers via linked devices, emails, IPs, payment methods, or addresses.
Session monitoring
Get a complete history of each user and company, down to individual page views and any custom actions.
Rule backtesting
Test complex risk logic on historical data first, ensuring zero disruption to legitimate users.
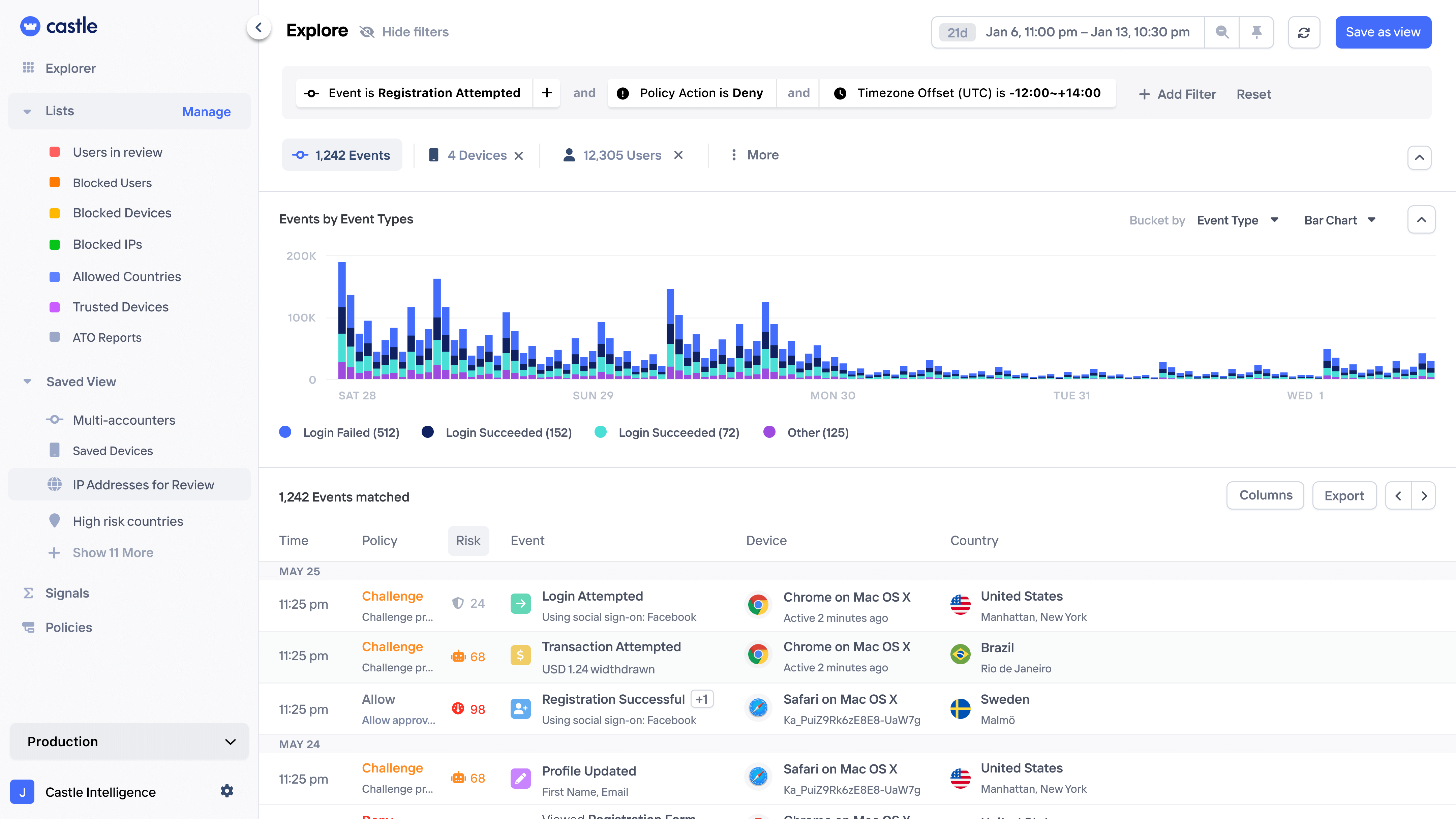
Pattern exploration
Uncover patterns in on login attacks, signup spam campaigns, and repetitive in-app transactions.
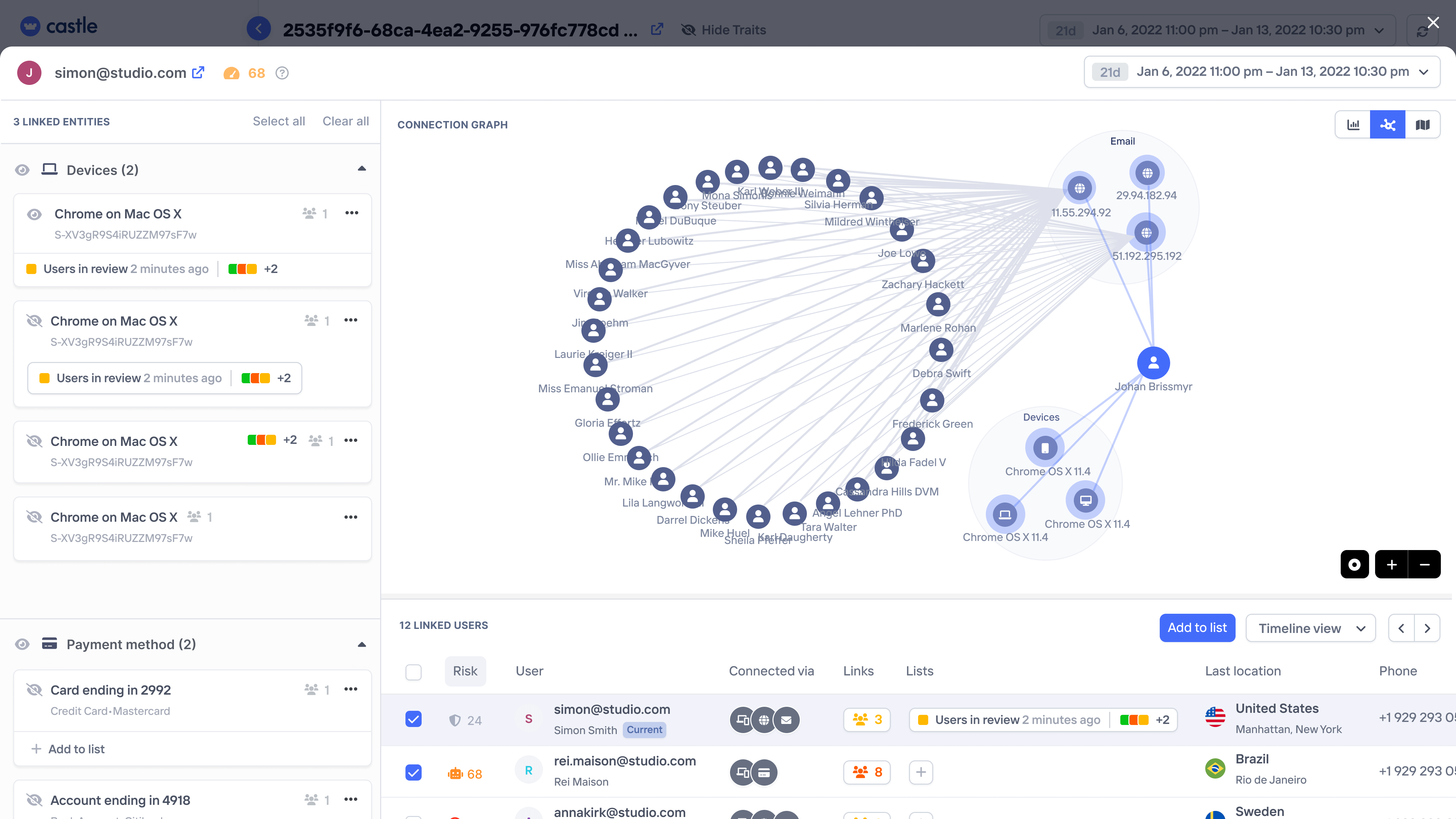
Network analysis
Spot interconnected users via shared devices, emails, IPs, payment methods, or addresses.
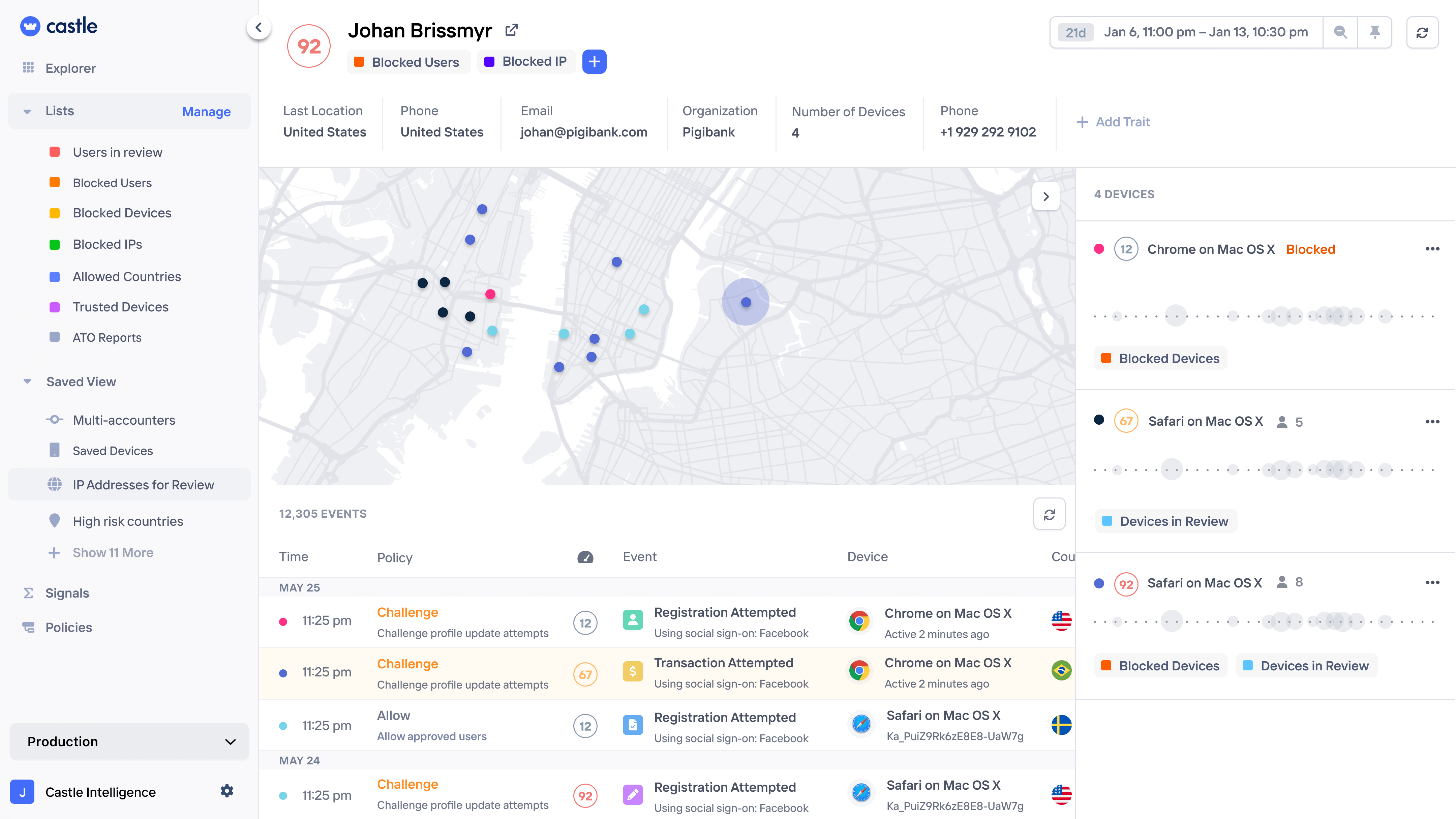
Session monitoring
Get a complete history of each user and company, down to individual page views and any custom actions.
Rule backtesting
Test complex risk logic on historical data first, ensuring zero disruption to legitimate users.
All the data you need to pinpoint account takeovers
Every interaction is enriched with comprehensive device intelligence, risk scores, location data, and much more.
Risk Scores
Out of the box risk scores for account abuse, account takeover, and bot abuse.
Velocities
Compute personalized signals based on real-time metrics like counts, sums, averages, and more.
Device fingerprinting
Persistent device identifiers resilient to storage resets and resistant to privacy plug-ins.
Bot detection
Identify bot actions via bot scores, headless indicators, or velocity and rate limit checks.
